Puzzel Microsoft Teams Azure authentication setup
Some features in Puzzel’s contact centre agent application requires users (agents) to authenticate themselves in Microsoft Entra ID (Azure AD). The authentication is amongst others used to enable contact search in Microsoft Teams but can also be used for authentication towards custom/external widgets.
This document shows a step by step description on how to configure Microsoft Teams in Microsoft Entra ID (Azure AD) to get the App ID URI required by the agent application for authenticating the user (agent).
Puzzel has made changes to the Application registration process from the first version to be in line with Microsoft recommendation for registering an app. We have support for user authentication with Authorisation Code Flow with PKCE according to Microsoft guidance. If you have registered with the old method we advise you to migrate to latest method as soon as possible as described below.
For more details on MSAL update from Microsoft read here.
Registering Microsoft Teams App in Azure
The following procedure will take you through the steps of configuring Microsoft Teams App in Microsoft Entra ID (Azure AD). At the end of this process, you will be given an App ID URI, required by the Agent Application for authenticating the agents.
Setup Microsoft Teams App in Azure
Step 1:
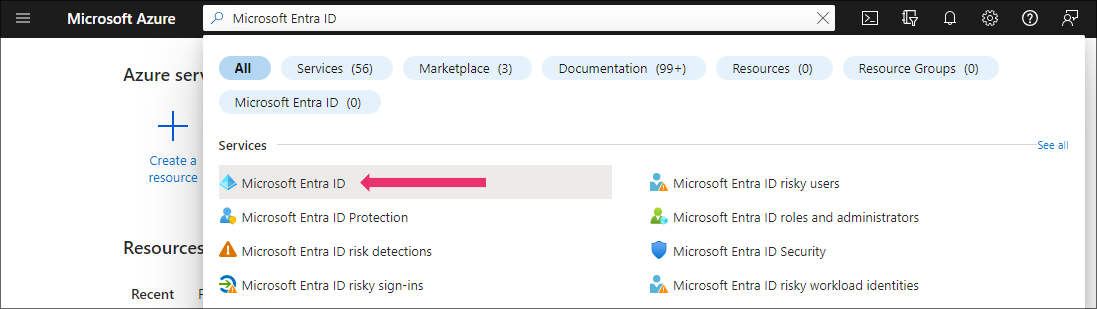
Go to https://portal.azure.com and login with the Global Admin privileges for your domain. Select “Microsoft Entra ID”.
Step 2:
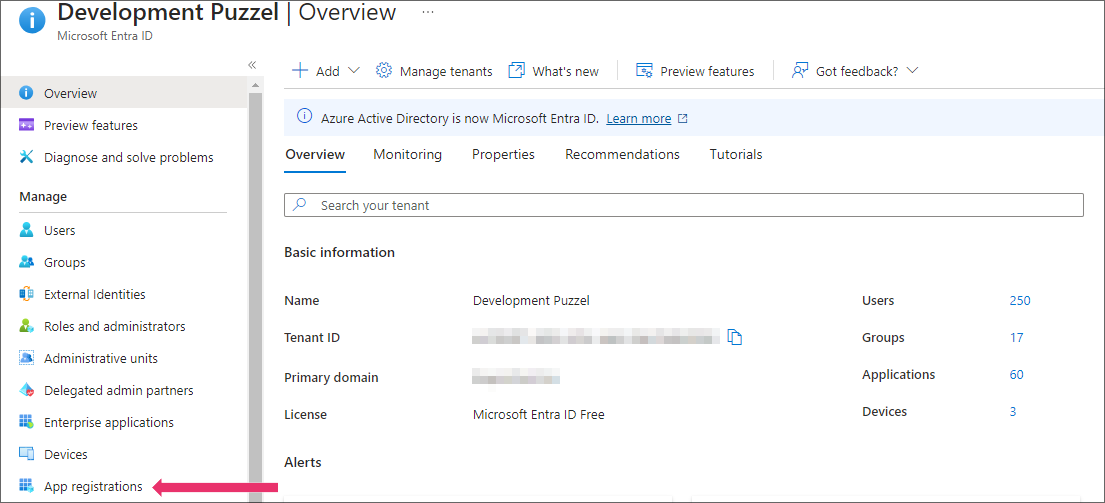
Select App registrations
Step 3:
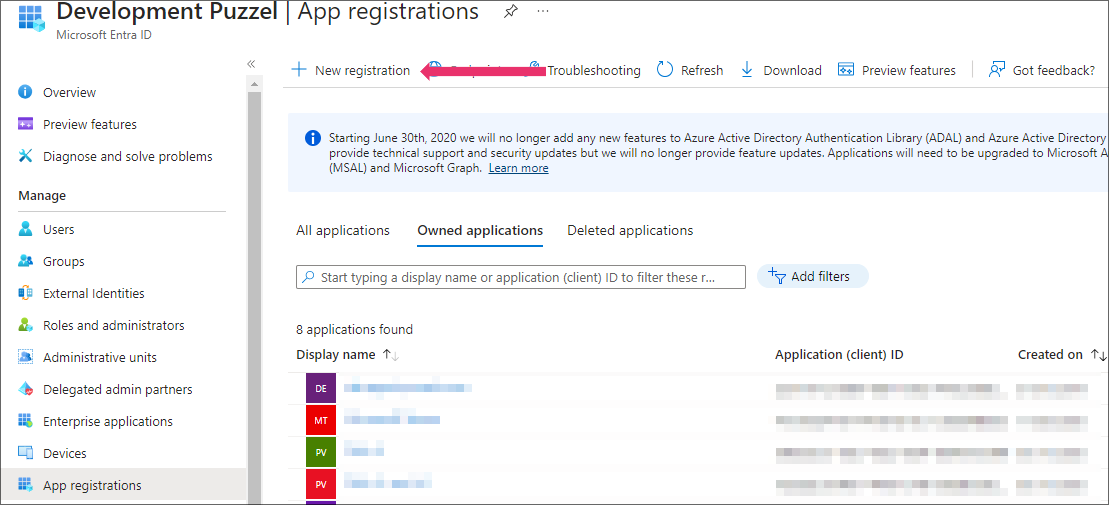
Click on the New registration option
Step 4:
Fill in the following 3 sections:
- Name - Choose a name for the application (e.g. Microsoft Teams)
- Supported account types – Choose the option that is relevant for you. The recommended option is “Accounts in this organisational directory only (<directory name>)
- Redirect URI (optional) – Choose "Single-page application" and ”https://app.puzzel.com/agent/" OR "https://uk.puzzel.com/agentapp/" for UK
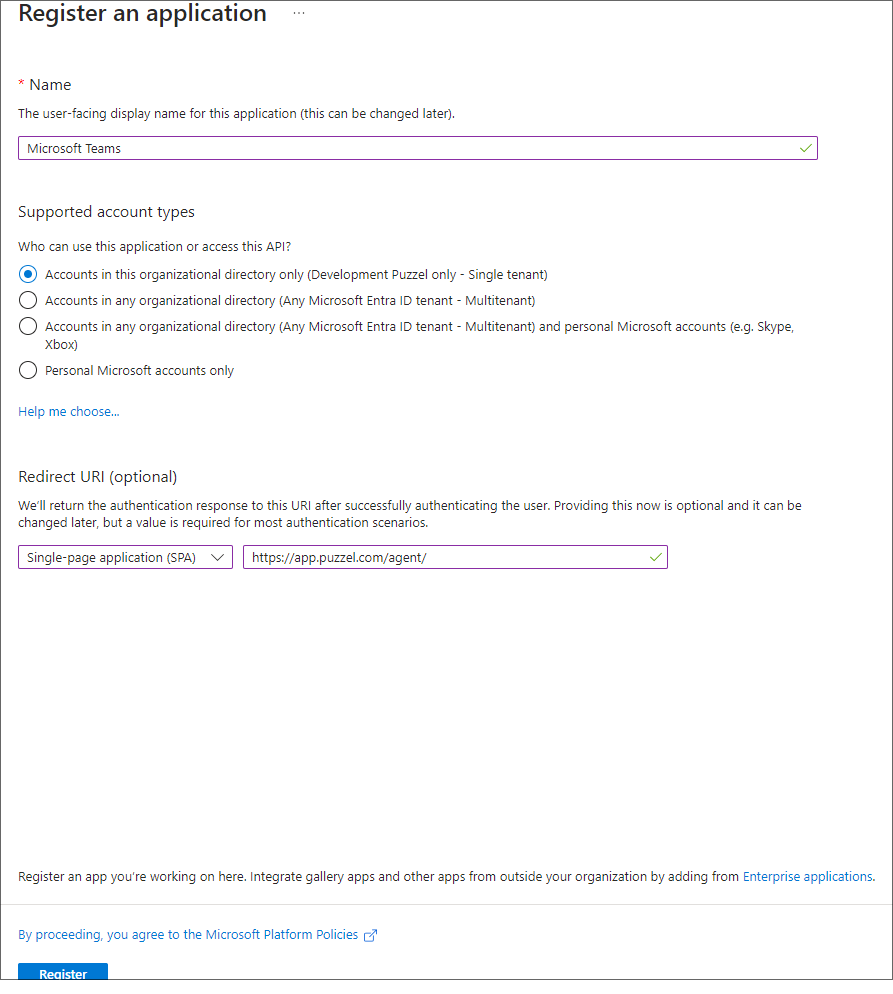
Click on the Register button. Now you should be able to see the given Application (client) ID you need for the admin portal later.
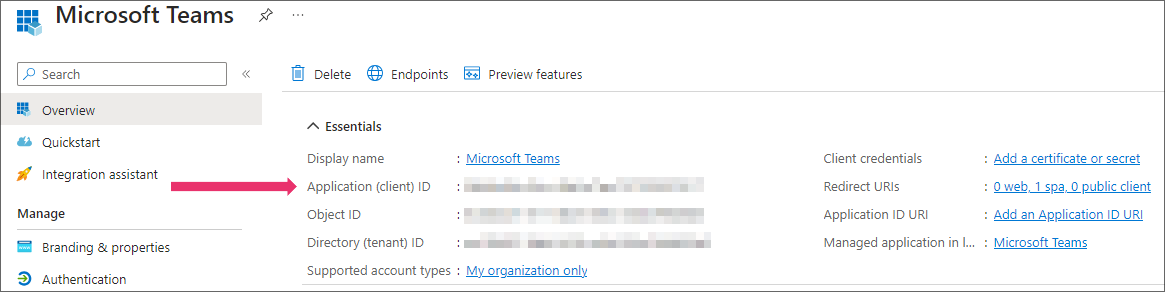
Step 5:
This section will help you configure all the required permissions for Microsoft Teams App. If you have Skype for business configured, some of the permissions will already exist. You will only need the additional ones required for Microsoft Teams.
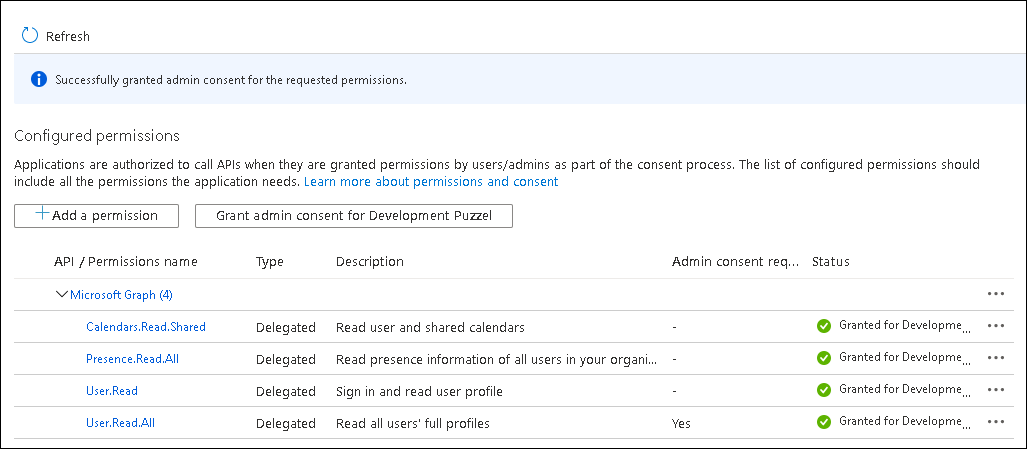
Add User and Teams presence permissions:
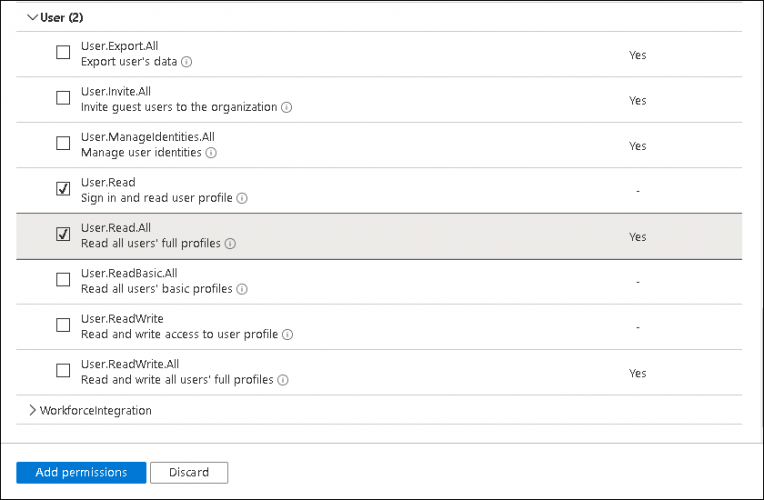
- Choose API permissions, click on the Add a permission button and select Microsoft Graph in the right pane. Choose Delegated permissions and select User. Tick the User.read and User.ReadAll check box.
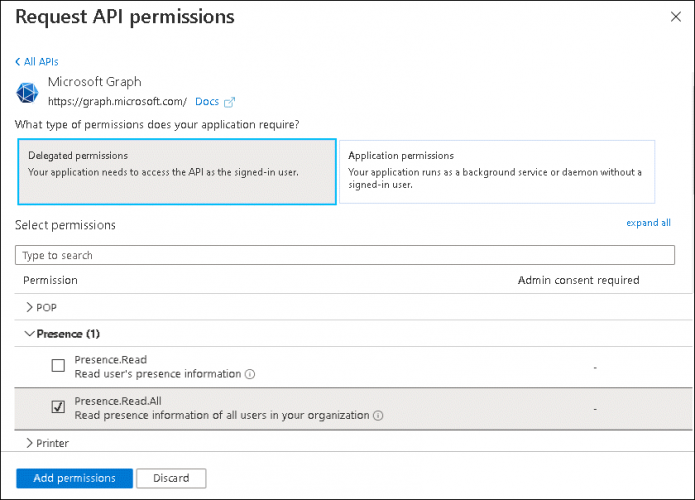
- Select Presence from the list and tick Presence.Read.All check box.
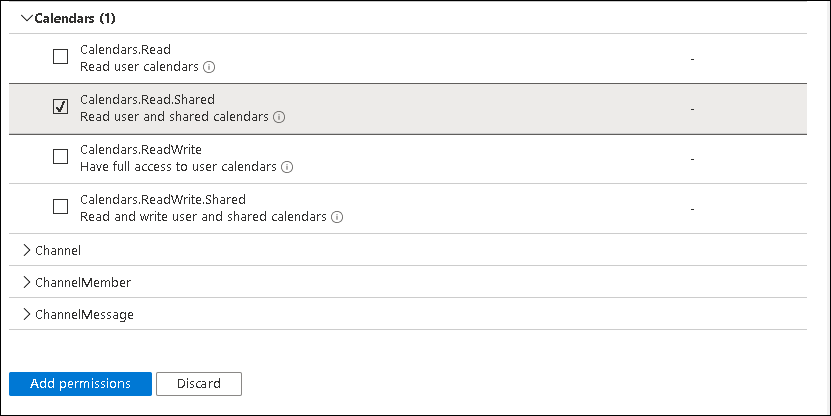
- Select Calendars and tick Calendars.Read.Shared check box
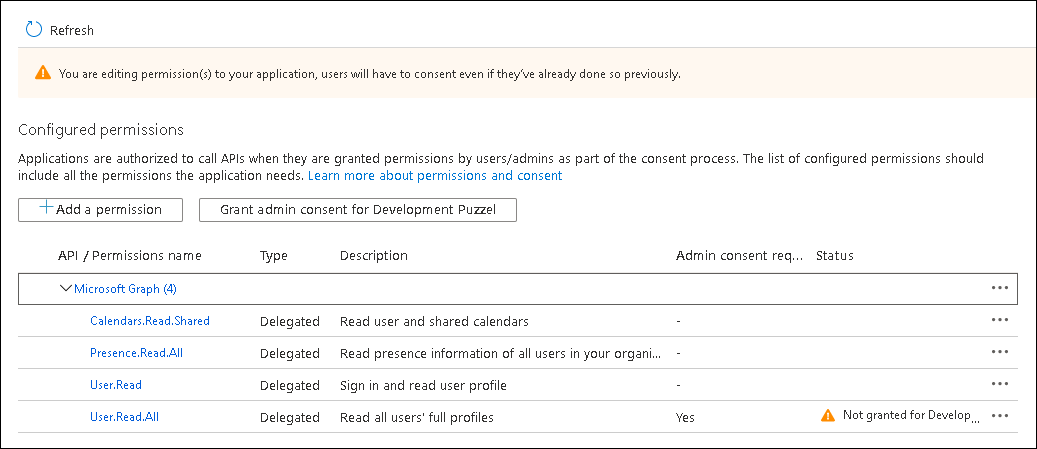
- Click on Add permissions.
Step 6:
Click on the Grant admin consent for <directory name> and click Yes to confirm
You should see a “Successfully granted admin consent for the requested permissions” confirmation at the top of the screen.
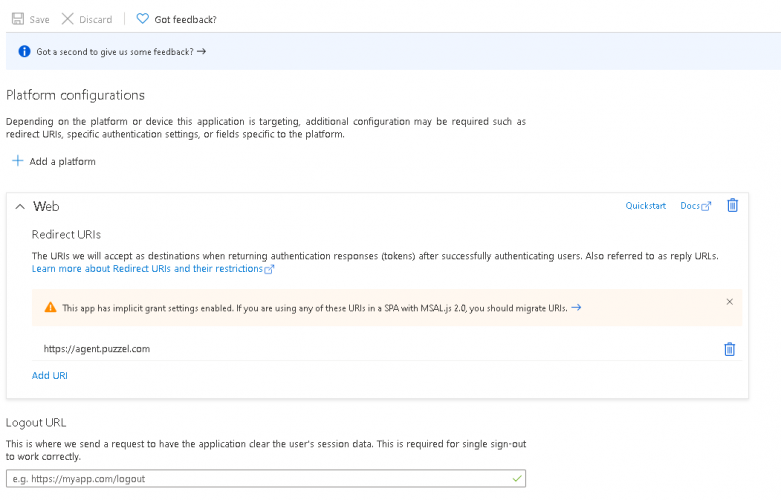
Step 7:
The last thing to do is to choose “Authentication” in the menu and add a Redirect URI if you are not yet using the agent application with Puzzel ID. Add "https://agent.puzzel.com" OR "https://uk.puzzel.com/agent/" for UK.
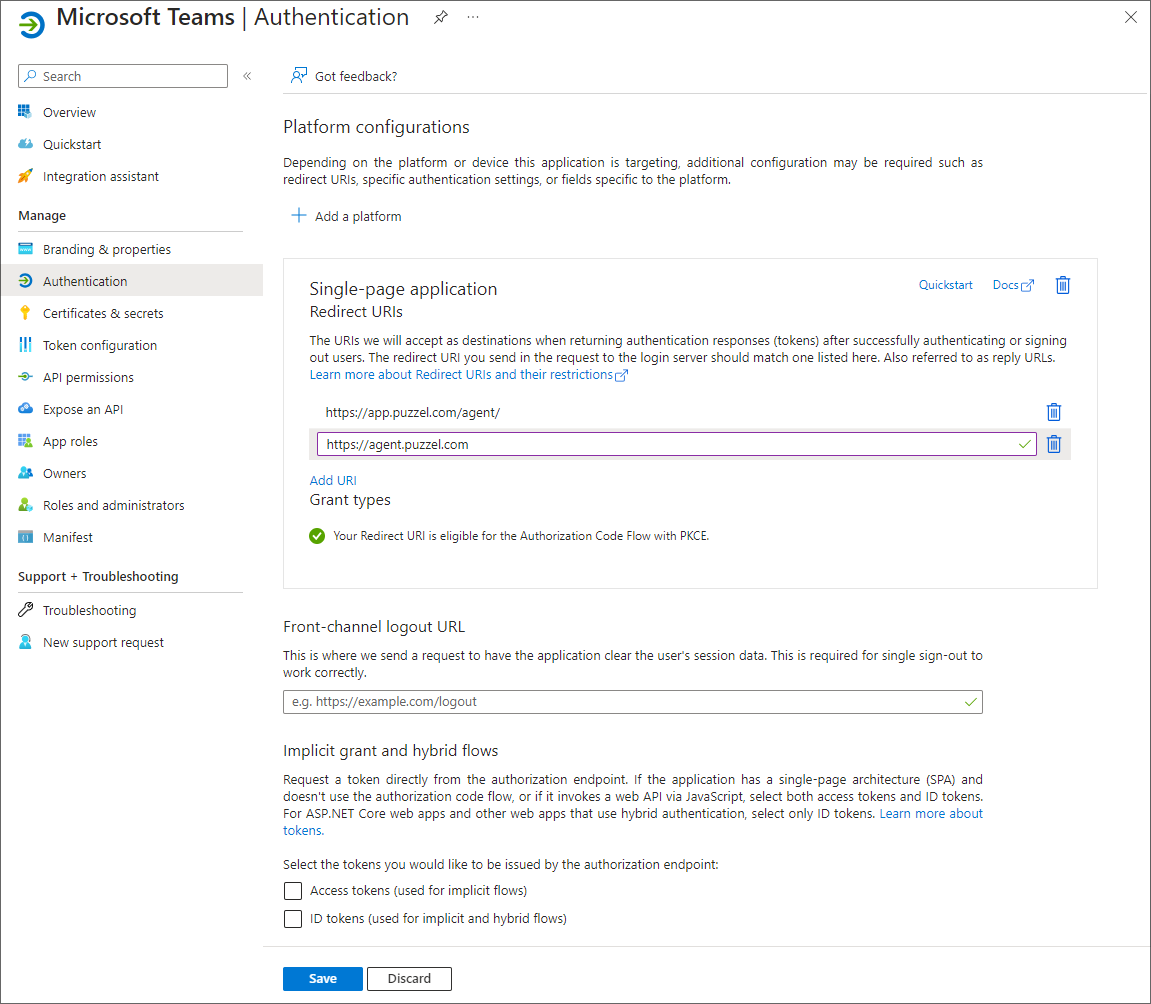
Migration from old method to latest method authentication:
As mentioned above we highly recommend our customers to migrate to latest authentication process. It can be done fairly easily by following the 4 steps listed below:
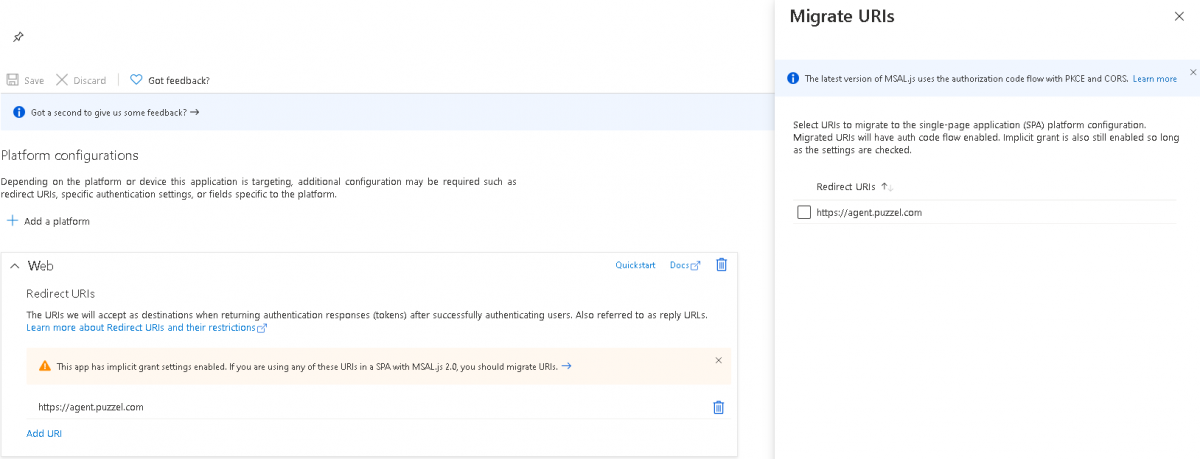
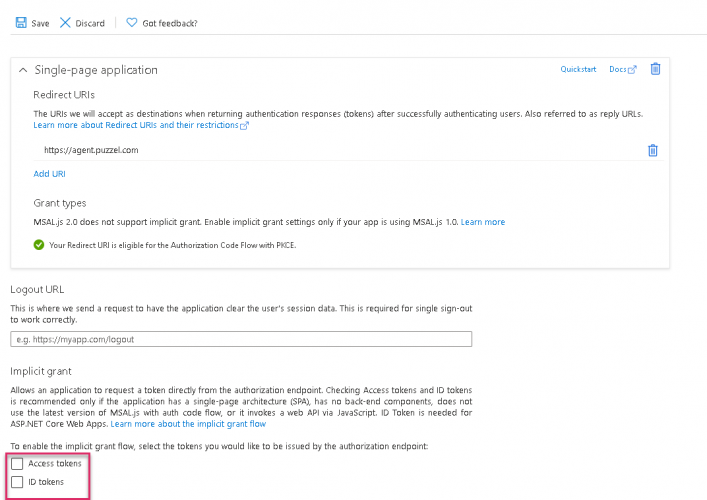
- Go to Authentication page and you will see the following warning as shown in the picture.
- Click on the warning to open the Migrate URIs window
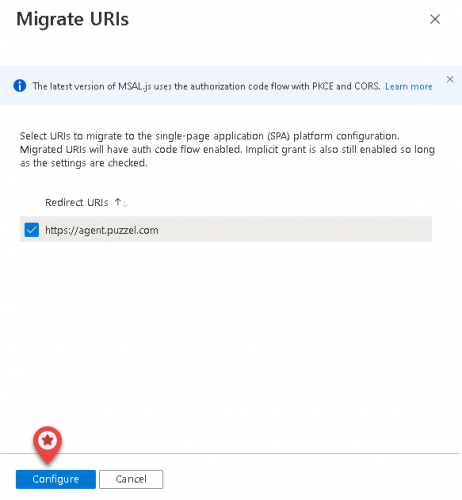
- Select the URI and click on Configure
- Add Redirect URI ”https://app.puzzel.com/agent/" OR "https://uk.puzzel.com/agentapp/" for UK as described in step 7 above.
- Untick the Access tokens and ID tokens under Implicit grant and save the changes.
Setup for Microsoft Teams integration in Puzzel’s admin portal
In the admin portal, you need to add your Microsoft Entra ID (Azure AD) app details for Microsoft Teams functionality to work properly.
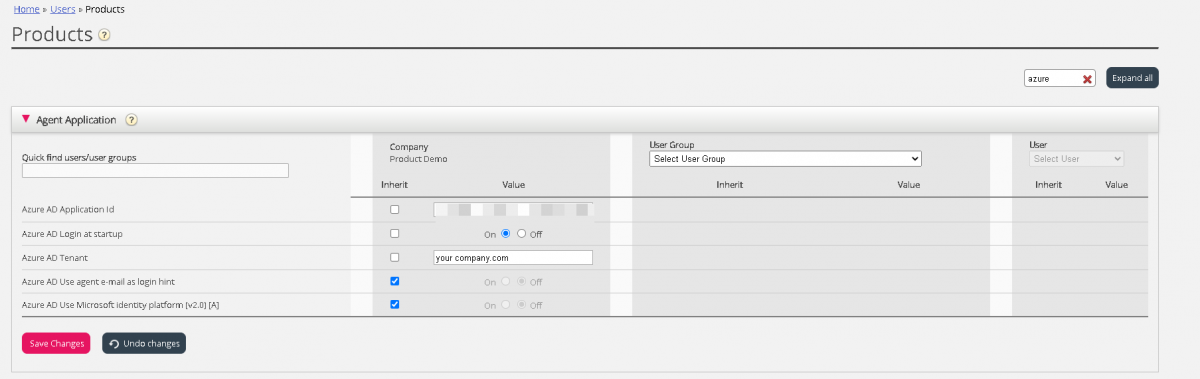
- Add the general agent application authentication properties for your Teams integration. This is done in the admin portal under Users -> Products -> Agent Application. The relevant 5 properties are easily found if you enter “Azure” in the top right filter field. If you have registered the app using old method in step 4, the configuration would be as shown below:
- Azure AD Login at startup – Enables to log on to Teams upon signing into the agent application, if authenticated.
- Azure AD Use agent e-mail as login hint – Upon authentication, the user’s e-mail address registered in his or her Puzzel account is suggested.
- Azure AD Application ID – Add the Azure App ID fetched from the Azure App setup
- Azure AD Tenant – Add your tenant/domain (without https://) for the directory used for fetching contact information.
- Azure AD use Microsoft identity platform[V2.0][A] - By default this property is turned off to enable the existing customers using the old method to continue without disruption to their services.
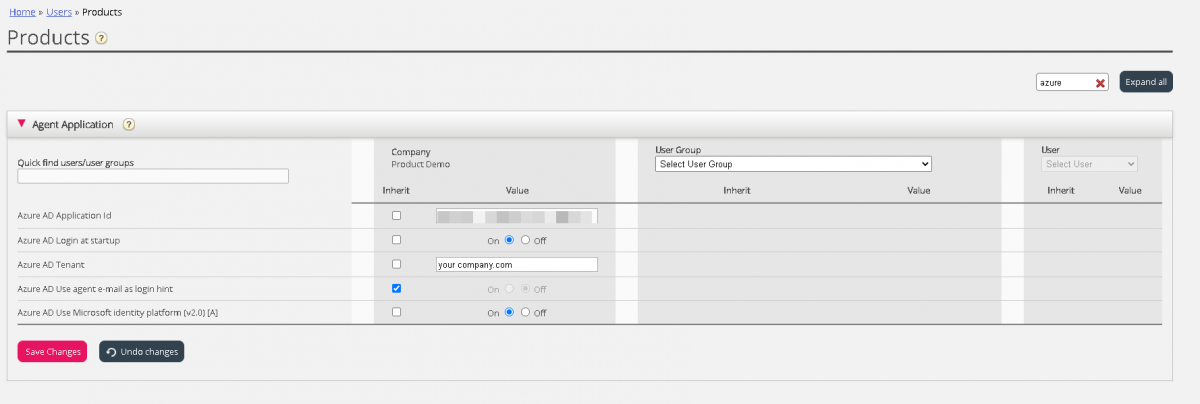
If you have registered the app using latest method in step 4, do the following:
- Azure AD Application ID – Add the Azure App ID fetched from the Azure App setup
- Azure AD Login at startup – Enables to log on to Skype for Business upon signing into the agent application, if authenticated.
- Azure AD Tenant – Add your tenant/domain (without https://) for the directory used for fetching contact information.
- Azure AD Use agent e-mail as login hint – Upon authentication, the user’s e-mail address registered in his or her Puzzel account is suggested.
- Azure AD use Microsoft identity platform[V2.0][A] - Turn this on for Microsoft recommended way of authentication using MSAL.
- Save your settings
- Activate the Microsoft Teams widget on your solution if you already haven’t. This is done under Widget -> Widget Administration. Find the “Microsoft Teams” widget (Owner 10000) and tick the rightmost check box
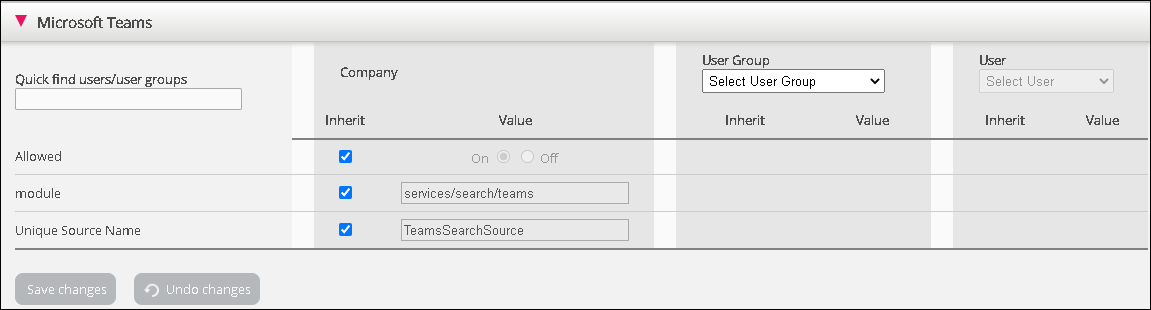
- The Microsoft Teams widget should now be available under Widget -> Widget Configuration -> Microsoft Teams. Unless you want to disable Microsoft Teams for some agents, you should use the default settings
- Allowed – Enable or disable Microsoft Teams features for users
- Module – System property. Do not change
- Unique Source name – System property. Do not change
- Remember to save your settings.
All users in your organization should now have access to search for your company’s Microsoft Teams contacts.
If not already authenticated, users are prompted to do so when signing in or searching for a contact in the Teams search source. They should then sign in with their corporate e-mail address.
Teams Presence
To enable synchronisation between Teams presence and Puzzel status you will need to enable the relevant admin permission. This is done under Users > Agent Application:
- Update presence on user from Microsoft Teams through Agent Application - Set this value to On